Cydney S. Posner is Special Counsel at Cooley LLP. This post is based on her Cooley memorandum.
At an open meeting on Wednesday last week, the SEC voted, three to two, to adopt final rules on cybersecurity disclosure. In his statement at the open meeting, Commissioner Jaime Lizárraga shared the stunning statistics that, last year, 83% of companies experienced more than one data breach, with an average cost of in the U.S. of $9.44 million; breaches increased 600% over the last decade and total costs across the U.S. economy could run as high as trillions of dollars per year. Given the ubiquity, frequency and complexity of these threats, in March last year, the SEC proposed cybersecurity disclosure rules intended to help shareholders better understand cybersecurity risks and how companies are managing and responding to them. Although a number of changes to the proposal were made in the final rules in response to objections that the proposal was too prescriptive and could increase companies’ vulnerability to cyberattack, the basic structure remains the same, with requirements for both material incident reporting on Form 8-K and periodic disclosure of material information regarding cybersecurity risk management, strategy and governance. According to SEC Chair Gensler, “[w]hether a company loses a factory in a fire—or millions of files in a cybersecurity incident—it may be material to investors….Currently, many public companies provide cybersecurity disclosure to investors. I think companies and investors alike, however, would benefit if this disclosure were made in a more consistent, comparable, and decision-useful way. Through helping to ensure that companies disclose material cybersecurity information, today’s rules will benefit investors, companies, and the markets connecting them.”
Here are the final rule, the fact sheet and the press release.
Of course, the SEC’s concerns about cybersecurity disclosure are not new. In 2018, the SEC issued long-awaited guidance on cybersecurity disclosure. The guidance addressed disclosure obligations under existing laws and regulations, cybersecurity policies and procedures, disclosure controls and procedures, insider trading prohibitions and Reg FD and selective disclosure prohibitions in the context of cybersecurity. That guidance built on Corp Fin’s 2011 guidance on this topic (see this Cooley News Brief), adding, in particular, new discussions of policies and insider trading. While the guidance was adopted unanimously, some of the commissioners were not exactly enthused about it, viewing it as largely repetitive of the 2011 staff guidance—and hardly more compelling. (See this PubCo post.) Moreover, although there were improvements in disclosure following release of the guidance, concern mounted that company disclosures were not consistent, comparable or decision-useful, with “different levels of specificity regarding the cause, scope, impact and materiality of cybersecurity incidents.” In addition, cyber risks had escalated during and after the pandemic with more remote work, together with more widespread reliance on third-party service providers and “rapid monetization of cyberattacks facilitated by ransomware, black markets for stolen data, and crypto-asset technology.”
To address these concerns, last year, the SEC proposed amendments intended to enhance and standardize cybersecurity disclosure. (See this PubCo post.) In response, several commenters contended that the 2011 and 2018 guidance were “sufficient to compel adequate cybersecurity disclosure, obviating the need for new rules.” (Among those with that point of view was Commissioner Hester Peirce, as reflected below in her comments at the open meeting.) Other commenters disagreed, maintaining that the guidance was not “sufficient to provide investors with the material information they need.”
Importantly, in the adopting release, in response to commenters, the SEC emphasized, “that the final rules supplement the prior guidance but do not replace it. The final rules are aimed at remedying the lack of material cybersecurity incident disclosure, and the scattered, varying nature of cybersecurity strategy, risk management, and governance disclosure, the need for which some commenters confirmed.” In particular, the release highlights the many topics not covered by the new rules but discussed in the 2018 guidance, including incorporating cybersecurity-related information into risk factor disclosure, MD&A, business and, if relevant, legal proceedings. In addition, the 2018 guidance discussed the application of financial reporting and control systems in the context of cybersecurity incidents and their impact on the financial statements. The guidance is still in effect, the SEC underscored, notwithstanding the adoption of these new rules.
In an extensive discussion, the adopting release also contests the argument made in comments (and by Peirce) that the SEC does not have authority to regulate cybersecurity disclosure or adopt the final rules. The SEC disagreed, contending that “[d]isclosure to investors is a central pillar of the Federal securities laws.” The release identifies a variety of statutory authorities for SEC-mandated disclosure, asserting that their
“grants of authority are intentionally broad. Congress designed them to give the Commission, which regulates dynamic aspects of a market economy, the power and ‘flexibility’ to address problems of inadequate disclosure as they arose…. The Commission has long relied on the broad authority in these and other statutory provisions to prescribe rules to ensure that the public company disclosure regime provides investors with the information they need to make informed investment and voting decisions, in each case as necessary or appropriate in the public interest or for the protection of investors….Consistent with the statutory scheme that Congress enacted, the Commission has continued to amend its disclosure requirements over time in order to respond to marketplace developments and investor needs.”
Those who might profess that the SEC’s disclosure authority is “limited to specific types of information closely related to the disclosing company’s value and financial condition,” the SEC asserted, are “misstat[ing] the scope and nature of the Commission’s authority. There is a wealth of information about a company apart from that which appears in the financial statements that is related to a company’s value and financial condition, including the material risks (cybersecurity and otherwise) a company faces.”
Final Rules
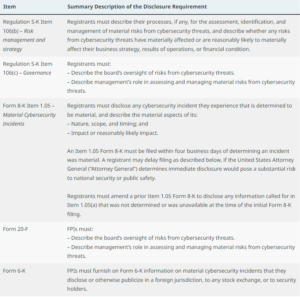
As described in the press release, the new rules adopted by the SEC last week require companies “to disclose material cybersecurity incidents they experience and to disclose on an annual basis material information regarding their cybersecurity risk management, strategy, and governance.” The final rules address cybersecurity disclosure from two perspectives: first, the rules require current disclosure about material cybersecurity incidents in new Item 1.05 of Form 8-K. Second, the rules require periodic disclosures, under Reg S-K Item 106, about a company’s “processes to assess, identify, and manage material cybersecurity risks, management’s role in assessing and managing material cybersecurity risks, and the board of directors’ oversight of cybersecurity risk.”
Here is the SEC’s table summarizing the new disclosure requirements:
Incident disclosure
Under the final rule, if a public company experiences a cybersecurity incident that the company determines to be material, the company is required to file a Form 8-K under new Item 1.05, describing the “material aspects of the nature, scope, and timing of the incident, and the material impact or reasonably likely material impact on the registrant, including its financial condition and results of operations.” The materiality determination regarding a cybersecurity incident must be made “without unreasonable delay” after discovery of the incident. To the extent that the required information has not been determined or is unavailable at the time of the required filing, the company is required to include a statement to that effect in the filing and then file an amendment to its Form 8-K containing that information within four business days after the company, without unreasonable delay, determines the information or the information becomes available.
Scope of disclosure. In response to comments, the final rule substantially narrows the nature and scope of the proposed disclosure. The original proposal had requested more detailed disclosure about the incident itself, including when it was discovered and whether it was ongoing, whether data was stolen or accessed, and whether it had been remediated. Commenters objected that, among other things, the information could actually assist threat actors, “exacerbate security threats, both for the registrants’ systems and for systems in the same industry or beyond, and could chill threat information sharing within industries.”
To provide a better balance, the final rule streamlines the required disclosure to focus primarily on the impact of a material cybersecurity incident rather than on requiring details about the incident itself. An instruction makes clear that the company is not required to disclose “specific or technical information about its planned response to the incident or its cybersecurity systems, related networks and devices, or potential system vulnerabilities in such detail as would impede the registrant’s response or remediation of the incident.” Although, in the final rule, the SEC did not adopt the proposed requirement to disclose remediation status and whether data were compromised, companies will still need to consider factors such as “data theft, asset loss, intellectual property loss, reputational damage, or business value loss” as part of their materiality analyses. The release also clarifies that the identification of “financial condition and results of operations” is just one type of impact and is not intended to be exclusive; the release advises that companies “consider qualitative factors alongside quantitative factors in assessing the material impact of an incident,” such as “harm to a company’s reputation, customer or vendor relationships, or competitiveness,” or the “possibility of litigation or regulatory investigations or actions.”
Commenters also raised issues regarding disclosure of incidents on third-party systems. Notwithstanding companies’ reduced control over those systems, the SEC decided to require companies to provide disclosures regarding cybersecurity incidents on the third-party systems they use. Similarly, the SEC did not provide a safe harbor for information disclosed about third-party systems. In the SEC’s view, data breaches may still be material even if the data were housed on a third-party system, especially as companies increasingly rely on third-party cloud systems. However, the SEC acknowledges that companies may have reduced visibility into third-party systems, and observes that companies are not required to “conduct additional inquiries outside of their regular channels of communication with third-party service providers pursuant to those contracts and in accordance with registrants’ disclosure controls and procedures.” Rather, companies are advised to “disclose based on the information available to them.”
Timing of disclosure. Commenters also objected to the proposed timing of incident disclosure, with many contending that the level of required detail was “impractical to produce in the allotted time,” and that the timing would lead to “tentative, unclear, or potentially inaccurate” disclosure and “false positives,” resulting in mispricing in the market. The SEC chose to retain the proposed timing, reasoning that the narrowed scope of disclosure would alleviate many of the timing concerns. Given that the new disclosure requirement focuses just on basic identifying details and material impact, the SEC concluded that the company “should have the information required to be disclosed under this rule as part of conducting the materiality determination.” Because, under the new disclosure requirement, companies will not need to disclose the “types of details that have the potential to be exploited by threat actors,” the SEC was not persuaded by any of commenters who sought to delay the timing “until companies mitigate, contain, remediate, or otherwise diminish the harm of the incident.” The SEC saw no reason to treat the timing for this 8-K item differently from others.
In response to comments, the SEC adopted a provision allowing delayed filing for an initial 30 days where the Attorney General determines that the disclosure poses a substantial risk to national security or public safety and notifies the SEC in writing. Further extensions of up to 120 days are possible; longer delays would require an SEC exemptive order. The release notes that the delay provision does not relieve a company’s obligations under Reg FD. The SEC advises that the staff have consulted with the DOJ “to establish an interagency communication process to allow for the Attorney General’s determination to be communicated to the Commission in a timely manner. The Department of Justice will notify the affected registrant that communication to the Commission has been made, so that the registrant may delay filing its Form 8-K.” The release observes that this delay provision is separate from Exchange Act Rule 0-6, which prohibits disclosure of classified information, and would take precedence over these cybersecurity disclosure rules.
Notwithstanding concerns raised by commenters about numerous conflicts with other Federal laws, such as the Cyber Incident Reporting for Critical Infrastructure Act of 2022 or HIPAA, the SEC found only one—the FCC’s notification rule for breaches of customer proprietary network information, which requires notification to the Secret Service and FBI within seven days of determination of a breach. The FCC rule further directs the entities to refrain from notifying customers or disclosing the breach publicly until seven business days after notification. The SEC has added a new instruction permitting companies subject to this rule to delay making a Form 8-K disclosure for up to the seven business days following notification to the Secret Service and FBI, with written notification to the SEC.
Materiality determination. The release advises that the concept of “materiality” in this context is consistent with caselaw in other securities contexts: “information is material if ‘there is a substantial likelihood that a reasonable shareholder would consider it important’ in making an investment decision, or if it would have ‘significantly altered the “total mix” of information made available.’”
Companies, the SEC advises, should assess the materiality of cybersecurity incidents (as well as risks and related issues) “through the lens of the reasonable investor. Their evaluation should take into consideration all relevant facts and circumstances, which may involve consideration of both quantitative and qualitative factors.” For example, a company assessing a data breach it has experienced should “consider both the immediate fallout and any longer term effects on its operations, finances, brand perception, customer relationships, and so on, as part of its materiality analysis.” The SEC explains that, because the analysis is fact-driven, “the same incident that affects multiple registrants may not become reportable at the same time, and it may be reportable for some registrants but not others.” In addition, the release confirms that “a decision to share information with other companies or government actors does not in itself necessarily constitute a determination of materiality.” The SEC also emphasizes “that ‘[d]oubts as to the critical nature’ of the relevant information ‘will be commonplace’ and should ‘be resolved in favor of those the statute is designed to protect,’ namely investors.”
As noted above, the new rule will require companies to determine the materiality of an incident “without unreasonable delay.” Commenters on the proposal had expressed concern that the proposed language requiring companies to make their materiality determinations “as soon as reasonably practicable” could create “undue pressure to make a materiality determination before a registrant has sufficient information to do so.” In response, the SEC revised the language in the instruction. The release offers some guidance illustrating how the SEC might interpret “without unreasonable delay.”
“For example, for incidents that impact key systems and information, such as those the company considers its ‘crown jewels,’ as well as incidents involving unauthorized access to or exfiltration of large quantities of particularly important data, a company may not have complete information about the incident but may know enough about the incident to determine whether the incident was material. In other words, a company being unable to determine the full extent of an incident because of the nature of the incident or the company’s systems, or otherwise the need for continued investigation regarding the incident, should not delay the company from determining materiality. Similarly, if the materiality determination is to be made by a board committee, intentionally deferring the committee’s meeting on the materiality determination past the normal time it takes to convene its members would constitute unreasonable delay. As another example, if a company were to revise existing incident response policies and procedures in order to support a delayed materiality determination for or delayed disclosure of an ongoing cybersecurity event, such as by extending the incident severity assessment deadlines, changing the criteria that would require reporting an incident to management or committees with responsibility for public disclosures, or introducing other steps to delay the determination or disclosure, that would constitute unreasonable delay.”
Updating amendments. Originally, the SEC had proposed to require that cybersecurity disclosure be updated in periodic reports to provide information that may not have been known at the time of filing. In addition, the proposed rules would have required disclosure in the next periodic report when a series of previously undisclosed individually immaterial cybersecurity incidents became material in the aggregate. That’s all been jettisoned in the final rule.
Instead, the new rule provides that updated incident disclosure be disclosed in Form 8-K amendments. A new instruction has been added directing the company, when information required under Item 1.05 is not determined or available at the time of filing, to include in its Item 1.05 disclosure a statement identifying any information called for in Item 1.05(a) that is not determined or is unavailable at the time of the required filing and then file an amendment to its Form 8-K containing that information within four business days after the company, without unreasonable delay, determines the information or it becomes available. (The release provides a reminder that the company may also have a duty to correct information that was incorrect at the time or a (widely disputed) duty to update disclosure that becomes materially inaccurate after it is made.) The SEC advises that companies “consider whether they need to revisit or refresh previous disclosure, including during the process of investigating a cybersecurity incident.”
SideBar
If they don’t have one already, companies should consider adding a process to their cybersecurity policies and procedures for assessing materiality “without unreasonable delay” and, to make clear when a Form 8-K filing is triggered, signifying a materiality determination, including which person or group will be responsible for making the determination. A similar process should be developed for assessing and determining materiality, “without unreasonable delay,” of updated information that was omitted from the original Form 8-K and may need to be added by amendment. Will board or board committee action be required or will the decision lie with management or other personnel alone? The release notes that Item 1.05 “does not specify whether the materiality determination should be performed by the board, a board committee, or one or more officers. The company may establish a policy tasking one or more persons to make the materiality determination.” In addition, as the releases advises, “[c]ompanies should seek to provide those tasked with the materiality determination information sufficient to make disclosure decisions.” It’s worth noting here that the SEC has brought several enforcement actions against companies for inadequate disclosure controls in the context of cybersecurity incidents. (See this PubCo post and this PubCo post.)
Instead of requiring aggregation of immaterial incidents as proposed, the SEC instead points to its revised definition of “cybersecurity incident,” which, in the final rule, now includes “a series of related unauthorized occurrences” and is to be “construed broadly.” The definition is intended to address the concept that “cyberattacks sometimes compound over time, rather than present as a discrete event” and may become material by a kind of accretion. What makes occurrences related? The SEC offers some examples: “the same malicious actor engages in a number of smaller but continuous cyberattacks related in time and form against the same company and collectively, they are either quantitatively or qualitatively material. Another example is a series of related attacks from multiple actors exploiting the same vulnerability and collectively impeding the company’s business materially.”
S-3 eligibility and liability exception. The SEC is amending Form S-3 to provide that the untimely filing of an Item 1.05 Form 8-K will not result in the loss of Form S-3 eligibility. In addition, the SEC is amending Rules 13a-11(c) and 15d-11(c) under the Exchange Act to include new Item 1.05 in the list of Form 8-K items eligible for the limited safe harbor from liability under Section 10(b) or Rule 10b-5 under the Exchange Act. The SEC believes that where the “the triggering event for the Form 8-K requires management to make a rapid materiality determination,” the safe harbor is appropriate. However, the Form 8-K must be filed, not furnished.
Periodic disclosure
The new rules require companies to provide annually in their Forms 10-K disclosure about risk management, strategy and governance regarding cybersecurity risks.
Risk Management and Strategy. Corp Fin’s experience has been that, although companies might include risk factors about cybersecurity risks, not many companies provide disclosure about cybersecurity risk oversight or any related policies and procedures. Accordingly, the SEC had proposed to require a description of policies and procedures for identification and management of cybersecurity threats and risks, as well as information about selection and oversight of third-party entities and how prior cybersecurity incidents affected the company. While some commenters favored the proposal, others were concerned about the prescriptiveness of the proposal, as well as the risk that the disclosure “could increase a company’s vulnerability to cyberattacks,” particularly “disclosures about whether cybersecurity policies are in place, incident response processes and techniques, previous incidents and what changes they spurred, and third-party service providers.”
The SEC heard the commenters’ concerns, acknowledging that extensive public disclosure of “how a company plans for, defends against, and responds to cyberattacks has the potential to advantage threat actors,” and, in response, narrowed the scope of the disclosure requirements to information material to investors, while “steering clear of security sensitive details.” The SEC also recognized that the rule could “unintentionally affect a registrant’s risk management and strategy decision-making,” and, in response, confirmed that that was not the intent.
The final rule (Reg S-K Item 106(b)(1)) requires a description of the company’s “processes, if any, for assessing, identifying, and managing material risks from cybersecurity threats in sufficient detail for a reasonable investor to understand those processes.” This revised formulation substitutes “processes” for “policies and procedures,” to “avoid requiring disclosure of the kinds of operational details that could be weaponized by threat actors, and because the term ‘processes’ more fully compasses registrants’ cybersecurity practices than ‘policies and procedures,’ which suggest formal codification.” The rule requires a description of cybersecurity processes to the extent they relate to material cybersecurity risks; the SEC expects that companies will tailor those processes to threats as they perceive them.
The final rule also eliminates many of the proposal’s more prescriptive requirements, changes that the SEC believes will help to avoid mandating disclosure of the kinds of operational details that could be weaponized and increase a company’s vulnerability to cyberattack. The final rule also adds a materiality qualifier. The SEC makes clear, however, that it still expects “the disclosure to allow investors to ascertain a registrant’s cybersecurity practices, such as whether they have a risk assessment program in place, with sufficient detail for investors to understand the registrant’s cybersecurity risk profile.” If a company discloses in risk factors indicating that it faces a material cybersecurity risk, the release states that “an investor can ascertain whether such risks have resulted in the adoption of processes to assess, identify, and manage material cybersecurity risks based on whether the company also makes such disclosures under the final rules.”
Although the final rule no longer identifies types of risks, in the release, the SEC provides guidance that risk types may include “intellectual property theft; fraud; extortion; harm to employees or customers; violation of privacy laws and other litigation and legal risk; and reputational risk.” The final rule also provides a pared-down non-exclusive list of topics the company should address, including:
“(i) Whether and how any such processes have been integrated into the registrant’s overall risk management system or processes;
(ii) Whether the registrant engages assessors, consultants, auditors, or other third parties in connection with any such processes; and
(iii) Whether the registrant has processes to oversee and identify such risks from cybersecurity threats associated with its use of any third-party service provider.”
he SEC advises that companies should also disclose any other information necessary for a reasonable investor to understand their cybersecurity processes. In the final rule, the SEC excluded a number proposed items about which commenters expressed concern, including prevention and detection activities, continuity and recovery plans and previous incidents. The final rule retains requirements to disclose information about engagement of third parties because the SEC considered it important “to know a registrant’s level of in-house versus outsourced cybersecurity capacity,” so that investors can assess a company’s cybersecurity risk profile.
New Reg S-K Item 106(b)(2) requires a description of “whether any risks from cybersecurity threats, including as a result of any previous cybersecurity incidents, have materially affected or are reasonably likely to materially affect the registrant, including its business strategy, results of operations, or financial condition and if so, how.” The SEC notes again, in this context, that companies may need to “consider whether they need to revisit or refresh previous disclosure, including during the process of investigating a cybersecurity incident.”
Although the SEC is not requiring Item 106 disclosures in registration statements, the release advises that companies “consider the materiality of cybersecurity risks and incidents when preparing the disclosure that is required in registration statements.”
Governance. The final rule requires a description of board oversight of risks from cybersecurity threats and management’s role in assessing and managing the company’s material risks from cybersecurity threats. The proposed rule would have specified more detailed disclosure requirements, such as how often the board discusses cybersecurity, how the board integrates cybersecurity into its business strategy, risk management and financial oversight, whether the company has a designated chief information security officer and to whom that individual reports. A number of commenters objected that the “disclosures would be too granular to be decision-useful.” In response, the SEC streamlined the disclosure requirement to make it “less granular than proposed.”
With regard to board oversight, the final rule eliminated many of more detailed requirements, specifying only that, in its description of board oversight, the company “identify any board committee or subcommittee responsible for the oversight of risks from cybersecurity threats and describe the processes by which the board or such committee is informed about such risks.” Although the express requirement was eliminated, as appropriate, the company could decide to disclose the frequency of reports to the board.
Also eliminated was a proposed requirement for disclosure about the cybersecurity expertise, if any, of board members, including a non-exclusive list of criteria to be added under Reg S-K Item 407(j). Apparently, there was a lot of pushback on this provision, with commenters contending that the rule was “overly prescriptive and in effect would direct how companies operate their cybersecurity programs.” For example, some commenters argued that “cybersecurity risk is not intrinsically different from other risks that directors assess with or without specific technical expertise,” and that companies would feel pressured to put cybersecurity experts on their boards—but there aren’t enough experts to go around. In the end, the SEC was convinced by commenters that “effective cybersecurity processes are designed and administered largely at the management level, and that directors with broad-based skills in risk management and strategy often effectively oversee management’s efforts without specific subject matter expertise, as they do with other sophisticated technical matters.”
With regard to management’s role, the final rule identifies several disclosure elements in a “non-exclusive list” that companies should consider addressing, as applicable:
“(i) Whether and which management positions or committees are responsible for assessing and managing such risks, and the relevant expertise of such persons or members in such detail as necessary to fully describe the nature of the expertise;
(ii) The processes by which such persons or committees are informed about and monitor the prevention, detection, mitigation, and remediation of cybersecurity incidents; and
(iii) Whether such persons or committees report information about such risks to the board of directors or a committee or subcommittee of the board of directors.”
The SEC believes that the elements in the new rule balance “investors’ needs to understand a registrant’s governance of risks from cybersecurity threats in sufficient detail to inform an investment or voting decision with concerns that the proposal could inadvertently pressure registrants to adopt specific or inflexible cybersecurity-risk governance practices or organizational structures.”
Definitions. The SEC had proposed including three new definitions in Reg S-K Item 106(a): “cybersecurity incident,” “cybersecurity threat” and “information systems.” These definitions were adopted largely as proposed with some exceptions.
In the final rule, the term “cybersecurity incident” is defined to mean “an unauthorized occurrence, or a series of related unauthorized occurrences, on or conducted through a registrant’s information systems that jeopardizes the confidentiality, integrity, or availability of a registrant’s information systems or any information residing therein.” As discussed above, the final rule adds the phrase “or a series of related unauthorized occurrences” to the “cybersecurity incident” definition. Although several commenters objected to the use of the term “jeopardizes” in the definition, arguing that the definition should be limited to cases of actual harm and exclude incidents that had only the potential to cause harm. But the SEC elected to retain the word in the definition, contending that the definition is “operationalized” by Item 1.05, which is conditioned on the incident having been material to the company and would usually, but not always, involve actual harm. In addition, although rare, there may be instances “where the jeopardy caused by a cybersecurity incident materially affects the company, even if the incident has not yet caused actual harm.” The final rule also retains the proposed use of “unauthorized” in the definition, given that, in the SEC’s view, an accidental occurrence would be an unauthorized occurrence, necessitating a materiality analysis.
The other two definitions were adopted without notable changes. “Cybersecurity threat” is defined in the final rule as “any potential unauthorized occurrence on or conducted through a registrant’s information systems that may result in adverse effects on the confidentiality, integrity, or availability of a registrant’s information systems or any information residing therein.” “Information systems” is defined to mean “electronic information resources, owned or used by the registrant, including physical or virtual infrastructure controlled by such information resources, or components thereof, organized for the collection, processing, maintenance, use, sharing, dissemination, or disposition of the registrant’s information to maintain or support the registrant’s operations.” The word “electronic” was added to modify information resources.
SideBar
At an Investor Advisory Committee meeting held in 2022 to discuss, among other things, the SEC’s cybersecurity proposal, one of the panelists observed that the concept of an “incident” can be murky and may elicit different responses from different companies. As an example, one panelist asked if finding a set of back-up tapes that, under policy, should have been destroyed would be considered an incident? A challenge of defining an incident, according to the panelists, will be that not many companies have the type of in-house forensics necessary to investigate, and many companies may need to bring in outside expertise. A panelist advised that companies may want to create a playbook to set out what should be done to determine if an incident has occurred and conduct tabletop exercises to detect any gaps.
Foreign private issuers and other issuers. The SEC adopted as proposed disclosure requirements for FPIs “parallel” to those adopted for domestic issuers” in Reg S-K Items 106 and Form 8-K Item 1.05. The amendments to Form 20-F incorporate the requirements of Item 106 to disclose information regarding an FPI’s cybersecurity risk management, strategy, and governance. In addition, the final rule amends General Instruction B of Form 6-K to reference material cybersecurity incidents among the items that may trigger a current report on Form 6-K.
Asset-backed securities issuers are exempt from the final rules. The SEC did not adopt an exemption for smaller reporting companies, but they will have a longer compliance phase-in period for the incident disclosure requirements.
Inline XBRL. The final rule requires companies to tag the new disclosures in Inline XBRL, including by block-text tagging narrative disclosures and detail-tagging quantitative amounts, with a staggered compliance date of one year.
Compliance Dates
The final rules will become effective 30 days following publication of the adopting release in the Federal Register. With respect to Reg S-K Item 106 and the comparable requirements in Form 20-F, all registrants will be required to include these disclosures in their annual reports beginning with fiscal years ending on or after December 15, 2023. Compliance with the 8-K and 6-K incident disclosure requirements will be required for all registrants other than smaller reporting companies beginning on the later of 90 days after the date of publication in the Federal Register or December 18, 2023. SRCs will have an additional 180 days and must begin complying with Form 8-K Item 1.05 on the later of 270 days after the date of publication in the Federal Register or June 15, 2024.
With respect to compliance with Inline XBRL, all registrants must tag disclosures required under the final rules in Inline XBRL beginning one year after the initial compliance date for any issuer for the related disclosure requirement. More specifically, for Item 106 of Reg S-K, all registrants must begin tagging in Inline XBRL beginning with annual reports for fiscal years ending on or after December 15, 2024; for Item 1.05 of Form 8-K and Form 6-K, all registrants must begin tagging in Inline XBRL beginning on the date 465 days after the date of publication in the Federal Register or December 18, 2024, whichever is later.
At the open meeting
In his statement, Chair Gensler placed the rules in the context of a historical tradition. He observed that “Congress recognized the benefits to investors of current reporting in enacting the Sarbanes-Oxley Act of 2002. Through the Act, Congress required companies to ‘disclose to the public on a rapid and current basis such additional information concerning material changes in the financial condition or operations of the issuer… as the Commission determines … is necessary or useful for the protection of investors and in the public interest.’ In 2004, implementing Congress’s mandate, the Commission adopted rules expanding current reporting on a range of matters. Today’s rules will add material cybersecurity incidents to the list of current reporting requirements…. Over the generations, our disclosure regime has evolved to meet investors’ needs in changing times. Today’s adoption marks only the latest step in that long tradition.”
He also observed that the final rules were responsive to public comment, “streamlin[ing] required disclosures for both periodic and incident reporting. For example, the final rules will require issuers to disclose only an incident’s material impacts, nature, scope, and timing, whereas the proposal would have required additional details, not explicitly limited by materiality. In considering today’s cyber-related disclosure rules, I am guided by the concept of materiality. Our markets depend on a basic bargain: Investors get to decide which risks to take so long as companies raising money from the public make full, fair, and truthful disclosure. Thus, if an issuer has a material cyber incident, then under today’s final rules, the issuer will need to disclose material information about that material incident.”
Commissioner Peirce, who had voted against issuing the proposal, continued her opposition to the final rule, even though, she acknowledged in her dissenting statement, it was better than the proposal. In her view, the final rules “ignore both the limits to the SEC’s disclosure authority and the best interests of investors. Moreover, the Commission has failed to explain why we need this rule.” She noted that both Corp Fin and the SEC have issued interpretive guidance; if “companies fail to make the required disclosures about cyber risks or inform investors of a cyber incident in a timely manner, the Commission can bring an enforcement action based on existing disclosure obligations.” In her view, new regulations were not necessary. And these “overly prescriptive” rules are especially not necessary: the new rule “reads like a test run for future overly prescriptive, overly costly disclosure rules covering a never-ending list of hot topics.”
To Peirce, something else is “overly”: that’s the SEC’s overly expansive view of its authority. First, she said, the SEC “rejects financial materiality as the touchstone for its disclosures, and fails to offer in its place a meaningful intelligible limit to its disclosure authority.” Although the SEC has authority to “take actions in the public interest and for the protection of investors, those actions need to relate to our core mission. The release prescribes granular disclosures, which seem designed to better meet the needs of would-be hackers rather than investors’ need for financially material information.” Second, she believes the required disclosures are normative: “the SEC’s potentially non-material risk management and governance disclosures veer into managing companies’ cyber defenses; the new rule looks like a compliance checklist for handling cyber risk, a checklist the SEC is not qualified to write.” The mandatory disclosures “may serve to drive companies to spend resources on compliance with our rules and conformity with other companies’ disclosed practices, instead of on combatting cyber threats as they see fit.” Third, Peirce takes issues with the rule’s “overly narrow law enforcement exception and general refusal to take into account other cyber disclosure laws.” With regard to the AG exception, the rule provides for only a 30-day delay and “makes extensions difficult beyond the initial thirty days.” In addition, she contended, the rules fails to consider the mandates of other agencies.
In addition, Peirce contended that the SEC did not show appropriate concern for the costs of the new rules to investors; a “flexible, principles-based approach that allows for disclosures tailored to the issuer making them would be a better way to protect investors.” In addition, the “compliance timelines are aggressive even for large companies…. Companies will have only months to align their internal disclosure processes with the new incident reporting requirements.”
Of even greater concern to Peirce was
“the potential for the rule to aid cyber criminals. The strategy and governance disclosures risk handing them a roadmap on which companies to target and how to attack them. The 8-K disclosures, which are unprecedented in nature, could then tell successful attackers when the company finds out about the attack, what the company knows about it, and what the financial fallout is likely to be (i.e., how much ransom the attacker can get). The requirement to file an amended 8-K when new information comes in will provide the attacker regular updates on the company’s progress. The 8-K disclosures also will signal to other would-be attackers an opportune time to attack. The careful drafting necessary to avert some of these problems will be difficult in the four-day filing timeframe. The release at least acknowledges these possible adverse consequences of the new disclosures. Even as the new disclosures tip off informed cyber criminals, they might mislead otherwise uninformed investors without first-hand knowledge of cyber attacking. The fast timeline for disclosing cyber incidents could lead to disclosures that are ‘tentative and unclear, resulting in false positives and mispricing in the market.’”
Most interesting, however, were Peirce’s largely scripted questions for Erik Gerding, Corp Fin director, which went on for quite some time. (Based on my notes only, so standard caveats apply.)
- “What assurances do you have that the Attorney General will be able to act in the timeframe we established?” Gerding responded that the staff had consulted with the DOJ to establish an inter-agency process in which the DOJ would notify the company that it could delay filing.
- How does the company reach the DOJ in the four-day period? Gerding contended that companies are often in communication with the DOJ. (Really?)
- When a company has experienced a breach, it needs to devote time early on to containing its losses. Won’t these reporting requirements disrupt those containment and recovery processes? In Peirce’s words, “Are you concerned that companies in the midst of a cyber-attack will be hindered in their ability to respond by having to alert the attacker about what they know about the attack?” According to Gerding, if a company follows its disclosure controls and procedures, those activities should not be impeded. In addition, companies must first determine the materiality of the incident, so the reporting requirement will not kick in immediately in the hours right after the breach. And there is no timeline for determining materiality, just a requirement that there not be unreasonable delay in making that determination.
- Isn’t this type of 8-K different from the norm; here, a filing is required when the company may not yet have its arms around the problem? In her words, “Are you concerned that the short preparation time for the Form 8-K could result in investors receiving information that is inaccurate?” Gerding responded that, if there is a determination of materiality and not all the information is available at the time of filing, then companies should acknowledge that fact with a statement to that effect and provide that information in amendments within four business days after it becomes known.
- The final rules remove the proposed requirement to aggregate immaterial incidents. However, the rules require disclosure of cyber incidents, defining “cyber incident” to include “an unauthorized occurrence, or a series of related unauthorized occurrences. “Will companies, under this new approach, nevertheless have to develop new costly systems to track immaterial events? The Commission leaves ‘related’ undefined. How would you explain that term to a company trying to figure out whether to aggregate occurrences for purposes of figuring out whether to file an 8-K?” As examples, Gerding suggested that related occurrences could include a series of continuous incidents conducted by the same bad actor or a series of incidents attacking the same vulnerability.
- “‘Cybersecurity incident’ is defined to include anything that ‘jeopardizes’ information systems. Under this definition, a cybersecurity incident could occur whenever information is merely at risk even if not actually stolen. Won’t companies have difficulty tracking cybersecurity incidents, so broadly defined?” Gerding responded that the definition focuses on unauthorized occurrences, and these might, for example, affect the integrity or availability of the system.
- “The Small Business Administration wrote us a letter recommending that we publish a Supplemental Initial Regulatory Flexibility Analysis because the one in the proposing release ‘lacks essential information,’ including which small entities would be affected and adequate consideration of alternatives. Why didn’t we publish a supplemental IRFA?” The staff believes that the final analysis complies with the Regulatory Flexibility Act.
- “One commenter argued that the rules could make companies less nimble in updating cyber policies and procedures because they would have to simultaneously change their regulatory filing. Is this a concern?” Gerding responded that the rules were not intended to impact updating of policies.
- “The timelines set forth in the release for coming into compliance with these rules are aggressive. At least one commenter suggested a two-year compliance period, but we are requiring same-year compliance. How is that reasonable?” Gerding replied that they believe the compliance periods are reasonable.
In her statement, Commissioner Caroline Crenshaw observed that “cybersecurity breaches reported by public companies increased by nearly 600% in the last decade and the costs, borne by issuers and their investors, are estimated to be in the trillions of dollars per year in the U.S. alone. The numbers are staggering, and I’m cognizant that even those substantial measurements do not tell the whole story. Cybersecurity intrusions can go beyond the loss of sensitive information and related remediation; as we saw in the Colonial Pipeline intrusion in 2021, they can alter the normal course operations of complex, capital- and infrastructure-intensive businesses.” She emphasized that knowledge of cybersecurity threats and breaches is “essential” given that “breaches can (and do) result in loss of revenue, customers, and business opportunities. Those harms may be realized or they may be ongoing in the form of lost sensitive information, remediation costs, and losses in shareholder value.”
Nevertheless, according to commenters, “existing disclosure practices vary in substance, organization, and presentation, thus establishing a need for, and benefit of, comparable, reliable, and decision-useful disclosures to investors.” This rulemaking serves as an example “of how our continuous reporting framework incorporates emerging risks—just as it was intended to do.” For example, the final rule includes “the important first step of ensuring adequate disclosure of managements’ cyber expertise. Commenters of all stripes agreed cyber expertise at public companies is critical, and this new disclosure will help ensure investors understand what skillset management brings to bear on the day-to-day oversight and operations related to cyber risks and incidents.” Still, she advocated that the SEC “continue to consider further disclosures, such as whether there is cyber-related expertise on the board,“ a provision that was eliminated from the proposal in the final rules.
Commissioner Mark Uyeda lamented, in his dissenting statement, the shift from the principles-based guidance of 2018 to the highly prescriptive requirements imposed by the new rules. He observed that some commenters believed that the 2018 guidance “already compelled sufficient cybersecurity disclosure. Given this support for the existing guidance, today’s amendments could have addressed other concerns by making incremental changes to the Commission’s disclosure regime as it applies to cybersecurity. However, rather than using a scalpel to fine-tune the principles-based approach of the 2018 Interpretive Release, today’s amendments swing a hammer at the current regime and create new disclosure obligations for cybersecurity matters that do not exist for any other topic.” Cybersecurity is just one of many risks; in his view, the new rules elevate cybersecurity above other, perhaps more material, risks, in the absence of any reasoned explanation for that elevation. As an example, he cites the requirement to disclose detailed information about management’s role in assessing material risks from cybersecurity threats, including “disclosure equivalent to the resumes” of responsible management and committee members.
Further, the new rules “break new ground by requiring real-time, forward-looking disclosure,” that is, mandating forward-looking statements regarding the reasonably likely impact of a breach, including impact on the affected company’s financial condition and results of operations. In addition, “a company will be required to amend its Form 8-K to disclose any material impacts, or reasonably likely material impacts, that were not determined or were unavailable at the time of the initial filing. No other Form 8-K event requires such broad forward-looking disclosure that needs to be constantly assessed for a potential amendment.” Even material acquisitions do not require this type of “constant reassessment.”
He also took issue with the exception for national security and public safety, which provides for a maximum delay of 120 days. He contrasted that exception with Rules 0-6 and 171, which prohibit disclosure of classified information entirely. In this context, he questioned “the notion that a reasonable investor would be unwilling to sacrifice receiving information that may jeopardize national security or public safety.” Rather, he maintained, most investors hold a portfolio of securities, not just a single security. “Premature public disclosure of a cybersecurity incident at one company,” he suggested, “could result in uncertainty of vulnerabilities at other companies, especially if it involves a commonly used technology provider, resulting in widespread panic in the market and financial contagion. Early information is often incomplete and not correct. One only need to look at the regional banking crisis to see how speculation can destabilize entire sectors, or even the markets as a whole.”
Finally, he disagreed with the conclusion that the final rule is not a “major rule” under the Small Business Regulatory Enforcement Act, given the likely annual impact on the economy of over $100 million. Off-script, he asked the staff for additional information regarding fn. 131 and the interplay with Rule 0-6. Gerding replied that the new rule doesn’t change Rule 0-6, but offered further consultation with the staff.
In his statement, Commissioner Lizárraga observed that, notwithstanding data regarding the growth and cost of cyber incidents, “today, there are zero disclosure requirements that explicitly refer to cybersecurity risks, governance or incident reporting. The final rule will change that, and provide investors with more timely, standardized, and informative disclosures, which will reduce market mispricing and information asymmetries.” Currently, companies can cherry-pick their disclosures, “if they disclose at all.” The new specific disclosure requirements will “reduce the risk of adverse selection, and the potential mispricing of a company. Beyond the clear benefits to investors, the rule will also have broader, indirect benefits. For example, more timely reporting of cyber incidents can serve as an alert to companies in the same sector that malign actors are launching cyber-attacks. Such companies could have more time to raise their cyber defenses and to mitigate any potential damage. Consumers may also benefit through more informed decision-making about which companies to entrust with their sensitive personal information.”
With regard to concerns raised that “providing detailed disclosures of cyber incidents could provide a roadmap for future attacks,” Lizárraga pointed out that the final rule “does not require specific, technical information that would serve that harmful purpose. Instead, it is focused on what the material impacts, or reasonably likely material impacts, of the incident will be,” which could affect valuation and profitability. For example, he suggested, “even if not quantifiable, the risk that a large segment of customers will lose faith in a business’s ability to protect sensitive personal information may certainly be material to an investor’s decision to invest in a company. This is especially the case in our post-COVID world, where working people in our country spend ever greater amounts of time working remotely.”
 Print
Print